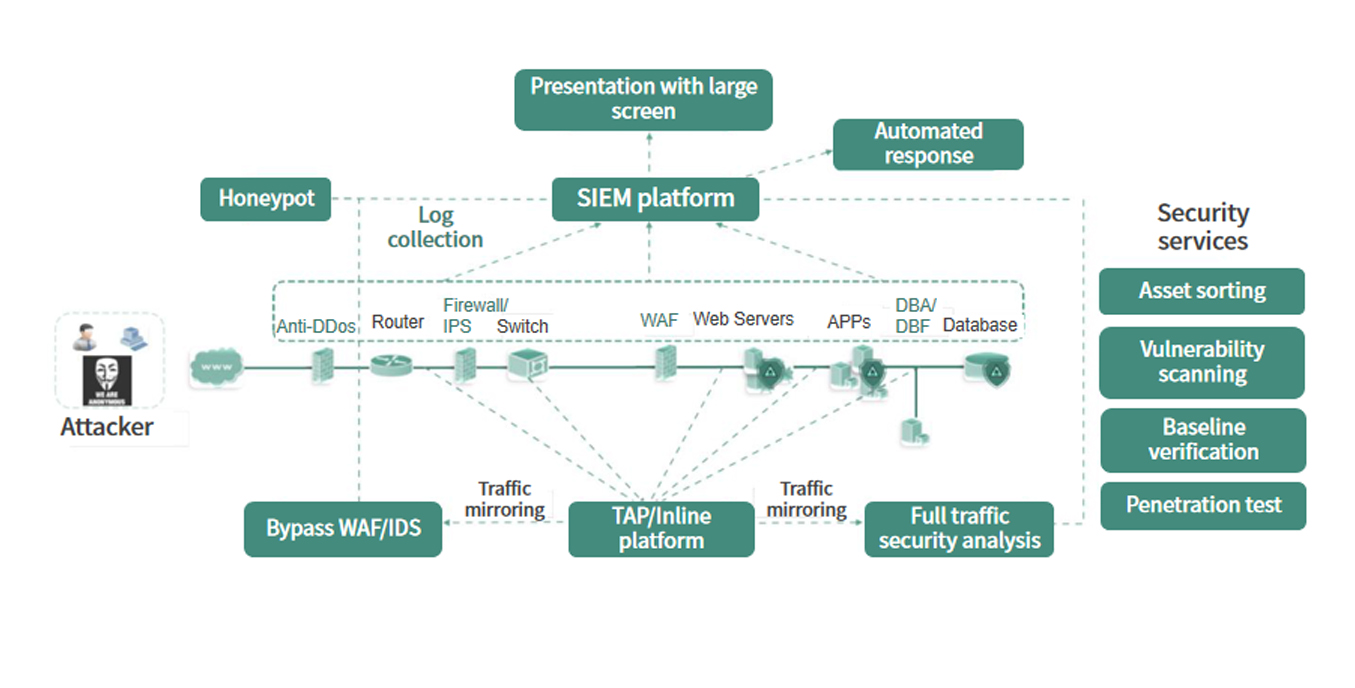
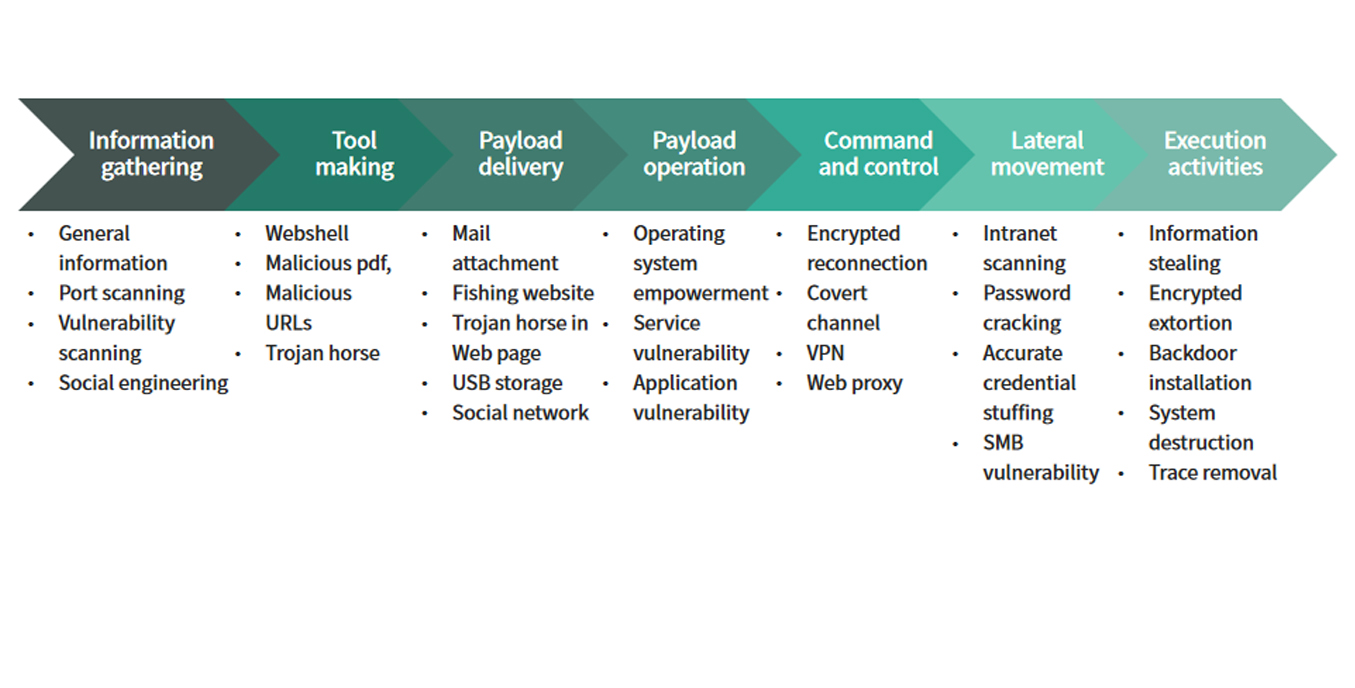
-

Perfect system
Build a full-fledged security protection system, check for leaks, fill in gaps, and ensure all-round, multi-dimensional security.
-
Security visualization
Establish a visual platform to present security attack and defense situations. Allow security engineers to have a clear understanding of potential security hazards.
-

Capability improvement
Through the practice and study of attack-defense confrontation, enhance the awareness and capability of attack-defense confrontation of security operations team, and solve internal security risks.
-

Security response
Form a standardized, efficient SIR process, take different measures for different security incidents, achieve early detection and early treatment, and minimize the impact on business.
About us
-
About us
-
News
Service
-
Smart Service
-
Service Solutions
Data Center Full-Stack IT Architecture Integration
Infrastructure Operations Insight Analysis and Optimization
Business Migration To A Hybrid Cloud Environment
IT Infrastructure O&M Services For Chinese Enterprises Going Global
IT On-site Services For Multi-Branch Organizations
Enterprise IPv6 Application Transformation Consulting And Implementation
-
Smart Cloud Services
Industry
-
Finance
Building Orchestratable Security Framework For Online Transactions
Low-Latency Trading Optimization Solution In Securities And Futures Markets
Network Construction Of Data Center Resource Pool
Backbone Network And Traffic Engineering
Full-stack IT For Urban Commercial Bank Data Centers
Building A BDR System For Data Center
-
Manufacture
-
Transportation
-
Operator
-
Government
-
Education
-
Enterprise