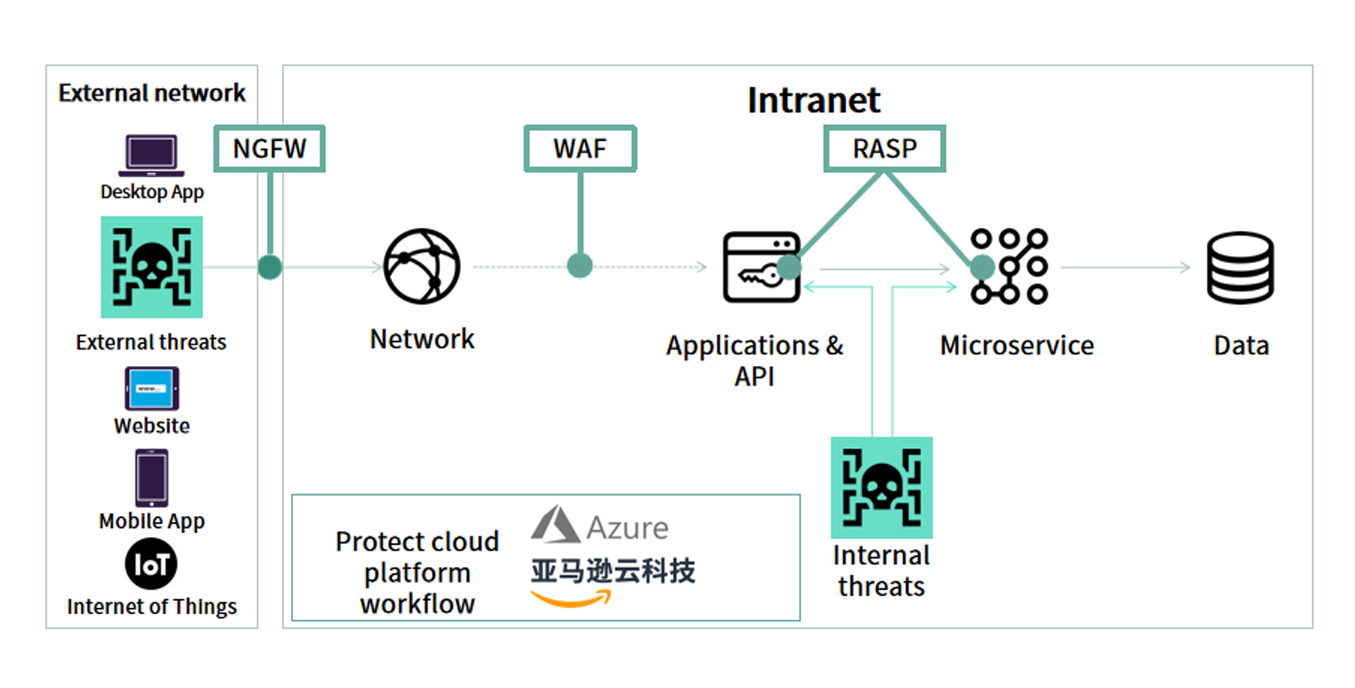
-

Web & API protection
Build perfect protection methods and systems for Web applications and APIs against mainstream Web application and API attack means, to protect Web servers and applications.
-

No business impact
After deploying security protection policies, enterprises need to ensure smooth operation of Web applications and avoid the impact of security protection policies on normal use of Web applications.
-

Prevention against malicious BOTs
In the face of malicious script, click farm, bonus hunter and other Bot behaviors, enterprise data is crawled, interfaces are brushed, etc., which brings high risks and incalculable losses to enterprises.
-

Tampering proof
Even without authorization, websites are vulnerable to data tampering, leading to the loss or destruction of important data.
About us
-
About us
-
News
Service
-
Smart Service
-
Service Solutions
Data Center Full-Stack IT Architecture Integration
Infrastructure Operations Insight Analysis and Optimization
Business Migration To A Hybrid Cloud Environment
IT Infrastructure O&M Services For Chinese Enterprises Going Global
IT On-site Services For Multi-Branch Organizations
Enterprise IPv6 Application Transformation Consulting And Implementation
-
Smart Cloud Services
Industry
-
Finance
Building Orchestratable Security Framework For Online Transactions
Low-Latency Trading Optimization Solution In Securities And Futures Markets
Network Construction Of Data Center Resource Pool
Backbone Network And Traffic Engineering
Full-stack IT For Urban Commercial Bank Data Centers
Building A BDR System For Data Center
-
Manufacture
-
Transportation
-
Operator
-
Government
-
Education
-
Enterprise